

Clubhouse is really hot recently, I spent few hours a day in the app, some of my friends actually bought iPhone due to FOMO! It has been long for an iOS user to feel exclusivity for having iOS only contents, the last was during the early Instagram time.
Being an app developer, we are trained to be curious, how to build an app like Clubhouse? Are there any naughty things that we can do?
With all these naughty ideas in mind, let’s do some reverse engineering.
Disclaimer: all information below is purely for education purpose, this post will be removed upon request
Part 1 (Decompilation)
The first thing to do is obviously downloading the IPA file. Some might not aware the way to download IPA file in the new iOS, you can use Apple Configurator to do so with some hacks! ( https://medium.com/@b0661064248/how-can-i-get-ipa-of-any-app-which-is-available-on-app-store-3a403be7b028 )
After we have the IPA, let’s decompile it and see what’s inside?
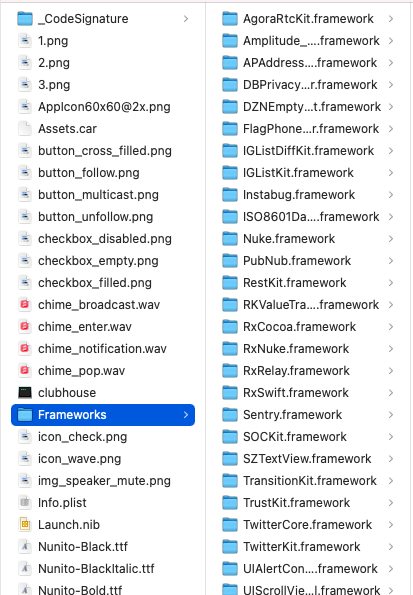
From here, it’s obvious that the app is built using native technology with a lot of native libraries! It doesn’t look good when seeing TrustKit library which is a SSL pinning library, which means we probably can’t use MITM Proxy or Charles for the next part on tapping the API. 🙁
We were reading news that tells Clubhouse is using Agora, from here we can verify they are! What are the other libraries used by Clubhouse?
If you are interested, you can use nm to grep information that you want. https://en.wikipedia.org/wiki/Nm_(Unix)
Part 2 (Traffic Interception)
Let’s use Men-In-The-Middle to tap the API request/response, MITM Proxy is a good library to do so ( https://mitmproxy.org/ and https://www.garyjackson.dev/posts/intercepting-ios-communication/) It can even support HTTPS traffic interception (provided no certificate pinning), where we have seen TrustKit in Part 1, but let’s try our luck.
After all setup, let’s see if we can get something! Unfortunately there is nothing except a report API to TrustKit telling someone trying to intercept and Amplitude (product analytic)
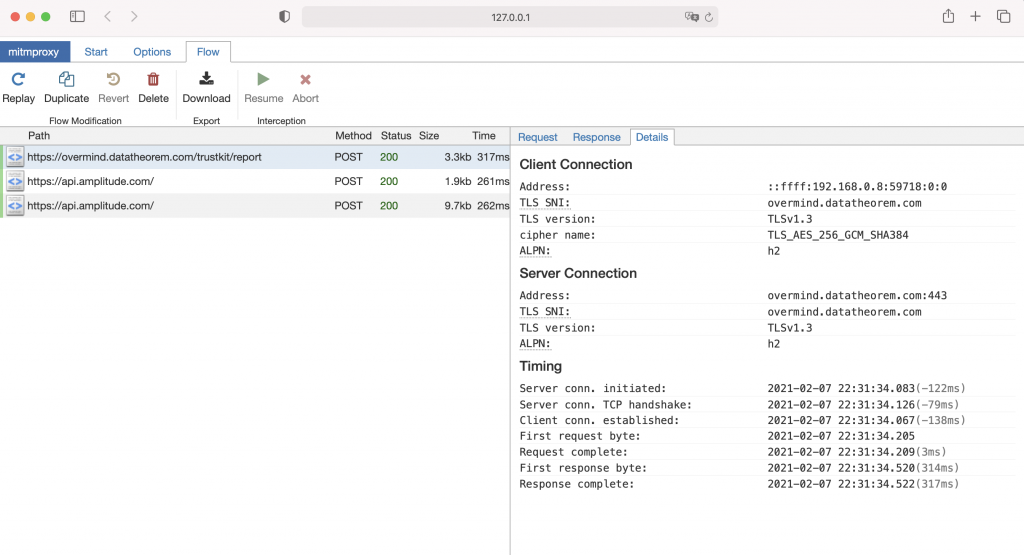
To ensure our setup is working, let’s try if other apps’ traffic can be intercept. It seems okay so Clubhouse traffic was blocked by TrustKit!

Part 3 (Try out the audio live engine)
Since the app is protected by TrustKit, it’s not so straightforward to intercept the traffic. When the Android version is launched, perhaps we can try using Frida, so we can tamper the app code at runtime. (If you familiar with mobile app pentest, you should be using a lot: https://frida.re/)
Then we decided to try out Agora, to see the complexity of integrating with them: https://docs.agora.io/en/All/downloads?platform=All%20Platforms
Since the iOS version is launched, so we have decided to try cross platform communication between native iOS and native Android. The example code is well written, basically we just need to replace the AppID and Token generated from the console, and we are good to go.
It’s just few lines of codes. Each room in Clubhouse is essentially a Channel, where it’s hardcoded in the demo code in our sample.

After compilation of both iOS and Android, we can indeed talk to each other just like Clubhouse magically! (Right from the simulator and emulator, you don’t even need a real device 🙂 )
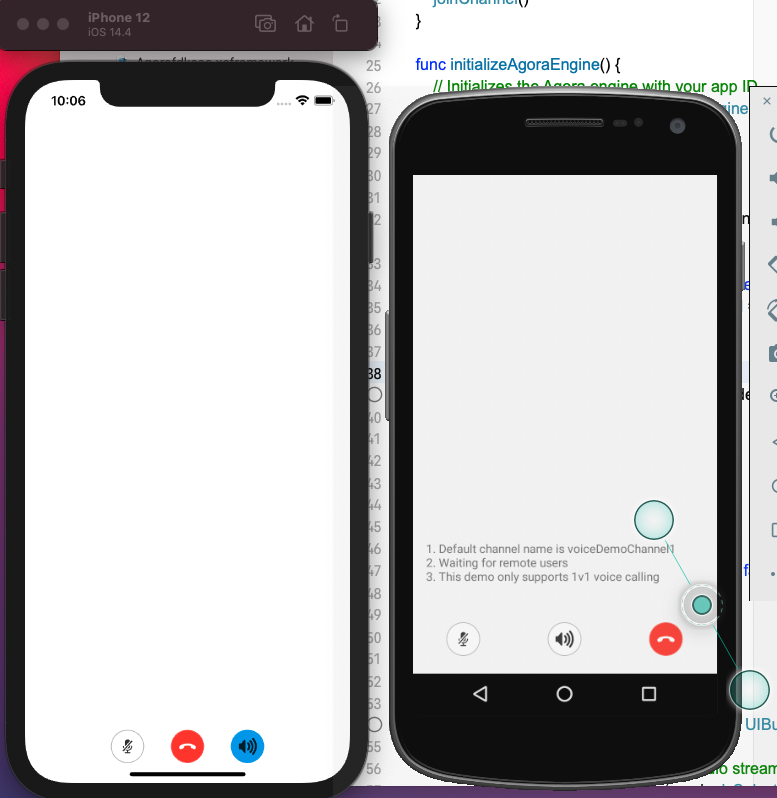
However, the demo web app shows “production version supports up to 17 participants”. In Clubhouse, the maximum participants are up to 5,000, not sure if it’s a billing limit or custom implementation by Clubhouse team.
After this exercise, we have the following conclusions: